So, in these times, Teams are becoming extremely popular and valuable for company’s with everybody working from home, and Microsoft giving away 6-months of free Teams licenses for new Tenants, it’s growing crazy fast. Its easy to get started, and users can create teams out-of-the-box🙈.
But for a few Administrators it can (In my own humble opinion, anyways) turn into a Wild West with out any form of control, with users creating new teams, as they like. (Why this isn’t a build in feature, and enabled by default, I don’t understand?🙄)
It might be an “old school” kind of thinking, but I would like some control over who does what in “my environment”.
I figured that others would be in the same situation, so I started my little adventure, in to figuring out how to “Lock-down” Teams, so that normal users wont be able to create what ever they want. You can do this in various ways, but the one I liked the most, is where you can control access to Teams creation through Group access. Fortunately for us, Microsoft has released an article on how to. You can read the original MS article HERE.
Lets get into it ![]()
First of, you need to log in to your Office 365 Tenant, with your Global Admin and create the security group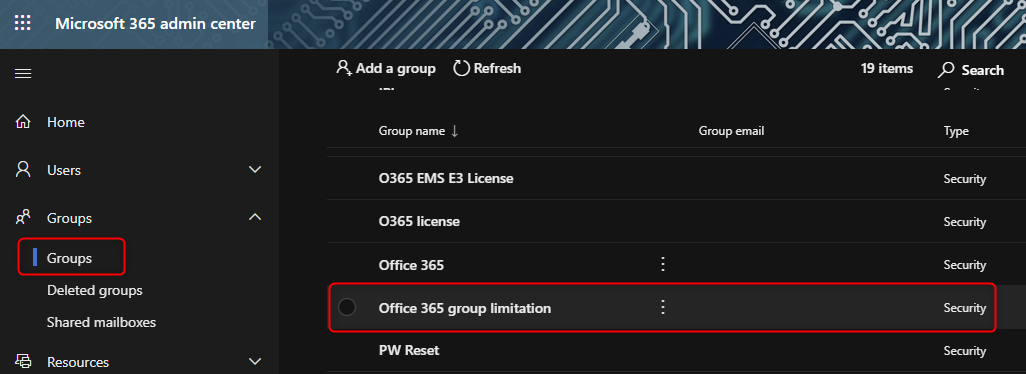 In my Example I created the group “Office 365 group limitation” Copy the below PowerShell script to your favorite editor, like Notepad, PowerShell ISE or Visual Studio Code. Name the script how you like, I kept it like MS suggested, GroupCreators.ps1
In my Example I created the group “Office 365 group limitation” Copy the below PowerShell script to your favorite editor, like Notepad, PowerShell ISE or Visual Studio Code. Name the script how you like, I kept it like MS suggested, GroupCreators.ps1
$GroupName = "Office 365 group limitation"
$AllowGroupCreation = "False"
Connect-AzureAD
$settingsObjectID = (Get-AzureADDirectorySetting | Where-object -Property Displayname -Value "Group.Unified" -EQ).id
if(!$settingsObjectID)
{
$template = Get-AzureADDirectorySettingTemplate | Where-object {$_.displayname -eq "group.unified"}
$settingsCopy = $template.CreateDirectorySetting()
New-AzureADDirectorySetting -DirectorySetting $settingsCopy
$settingsObjectID = (Get-AzureADDirectorySetting | Where-object -Property Displayname -Value "Group.Unified" -EQ).id
}
$settingsCopy = Get-AzureADDirectorySetting -Id $settingsObjectID
$settingsCopy["EnableGroupCreation"] = $AllowGroupCreation
if($GroupName)
{
$settingsCopy["GroupCreationAllowedGroupId"] = (Get-AzureADGroup -SearchString $GroupName).objectid
}
else {
$settingsCopy["GroupCreationAllowedGroupId"] = $GroupName
}
Set-AzureADDirectorySetting -Id $settingsObjectID -DirectorySetting $settingsCopy
(Get-AzureADDirectorySetting -Id $settingsObjectID).ValuesChange the Group name in the script, to the group name you created in the beginning. You will need your O365 Global admin, to run the script. Also if you haven’t already, you need to install the Azure AD module for PowerShell.
Install-Module AzureADPreviewIf you have the used the module before or maybe have the general availability version (2.0), make sure you either remove and reinstall or update it before continuing.
And you’re ready 👍 If you have a handful of users that you trust, you add them to the group, or maybe your Helpdesk workers, so that they can create Teams for the users.
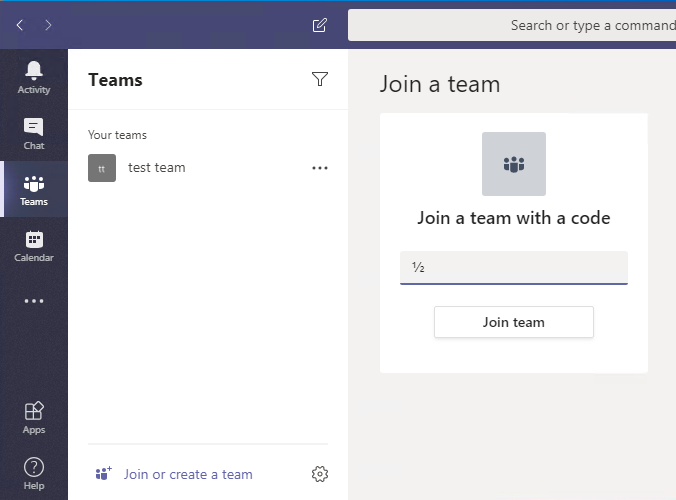
This is what it looks like now for the users!
Without group membership…
With group membership…
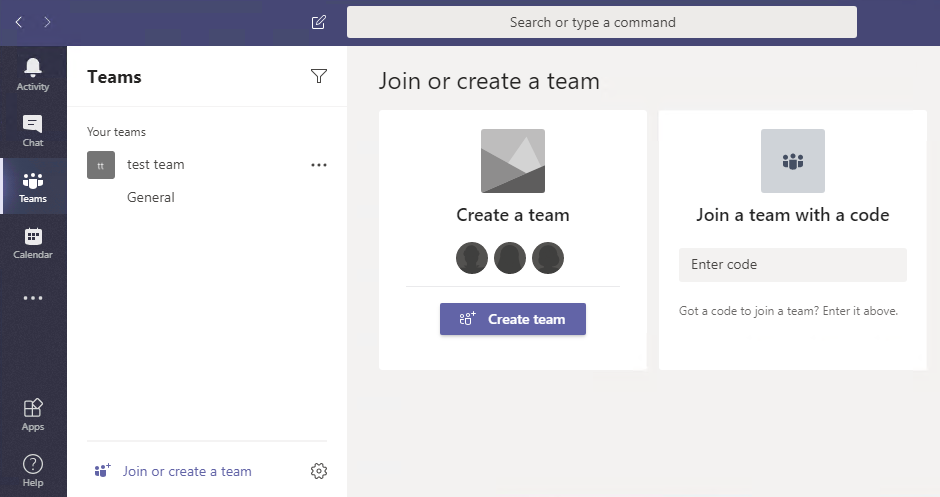
From now on, when users go to Teams and click the “Join or Create a team”, the only options is to join a team with a code or they can search for the Team, if they know the name. Here’s a few options:
- You as an admin, add them.
- You tell the newly appointed owner to add users themselves 👍
- The users search for the Team and join 👍
- Or you send them a Code, that they can use to join the Team with (Team owner can do this) 👍
That’s it, you’re done and have just a little more control with what’s going on again 😊